User Logoff
Enabled by default
Service: Microsoft Windows security auditing.
Log type: Security
A users log off can indicate the end of an attack or potential system restarts that may have occurred. This can conclude a timeline or give a bit more insight to a users activity. This log is recommended by the NSA Cyber Event Forwarding Guidance and JPCERT/CC.
Get-WinEvent -FilterHashTable @{LogName='Security';ID='4634'} -MaxEvents 1 | Format-Listauditpol /get /subcategory:"logoff"
auditpol /set /subcategory:"logoff" /Success:Disable /Failure:Disable
auditpol /set /subcategory:"logoff" /Success:Enable /Failure:Enable
Compliance
HIPAA
Level: Recommended
NSA Event Forwarding
Level: Recommended
https://github.com/nsacyber/Event-Forwarding-Guidance/tree/master/Events
Similar to User logon, Windows 10 professional does not log user logoffs of users automatically. To turn this on, follow the steps outlined in “User Login” to toggle login attempts.
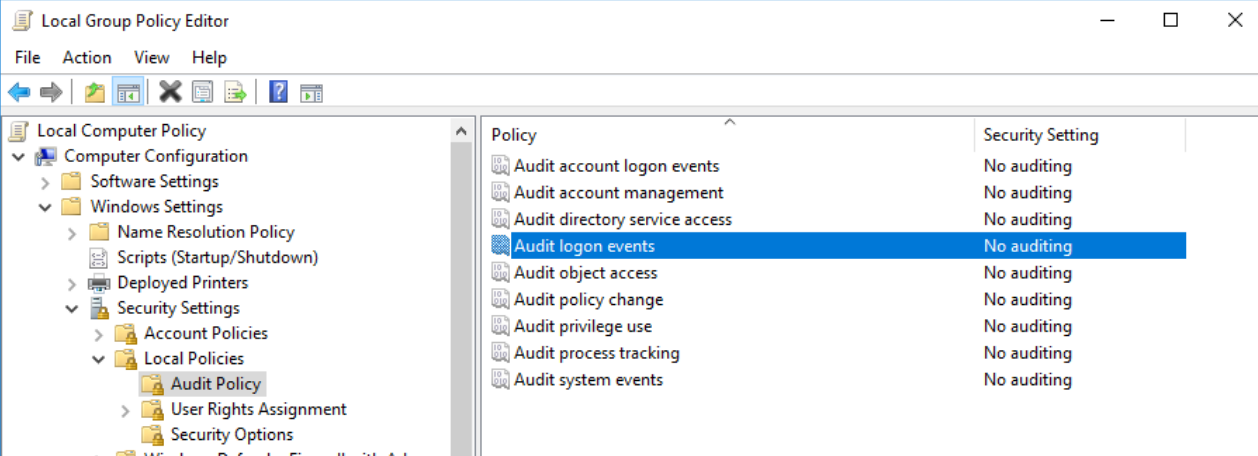
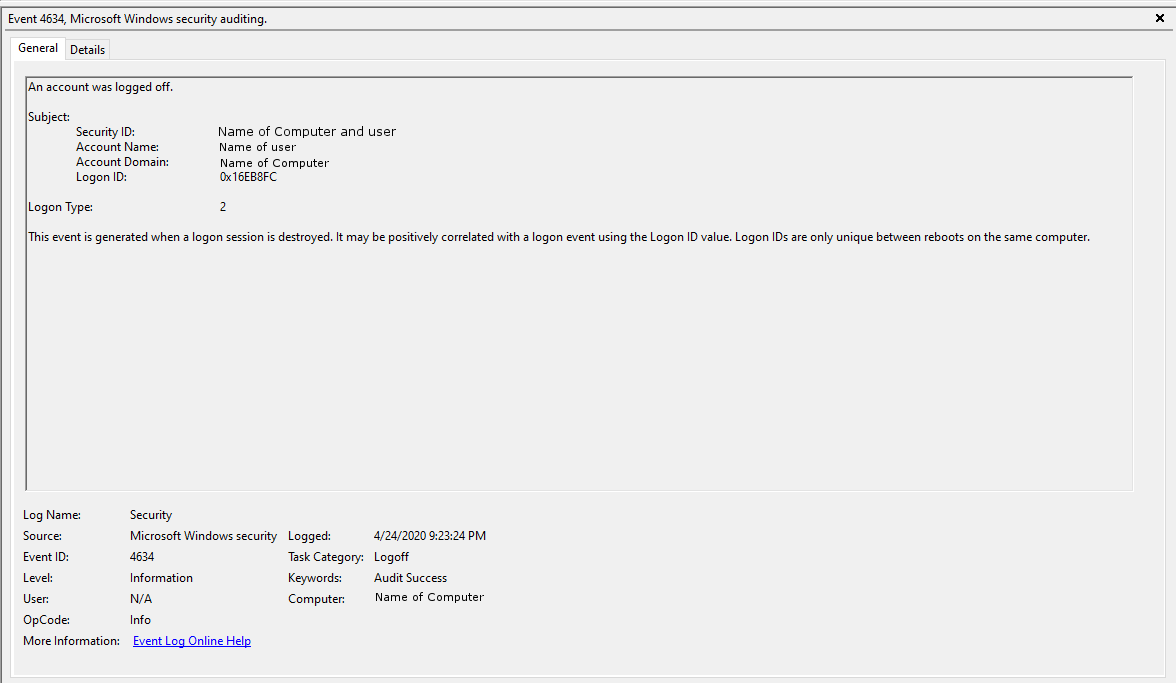
To view this log, navigate to the Event Log Viewer. From there, navigate to the Windows Logs heading and the Security tab. Filter, sort, or find the event log ID 4634 to view this log.
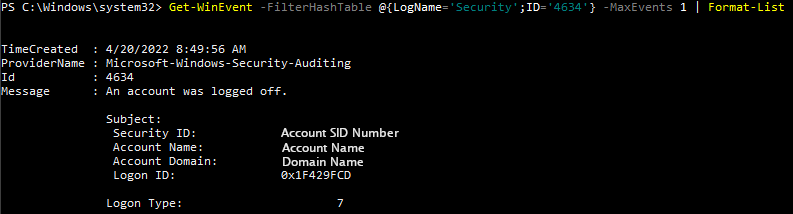
To view this log in the command line with Get-WinEvent, open PowerShell as an administrator. From here, enter the command Get-WinEvent -FilterHashTable @{LogName='Security';ID='4634'} -MaxEvents 1 | Format-List
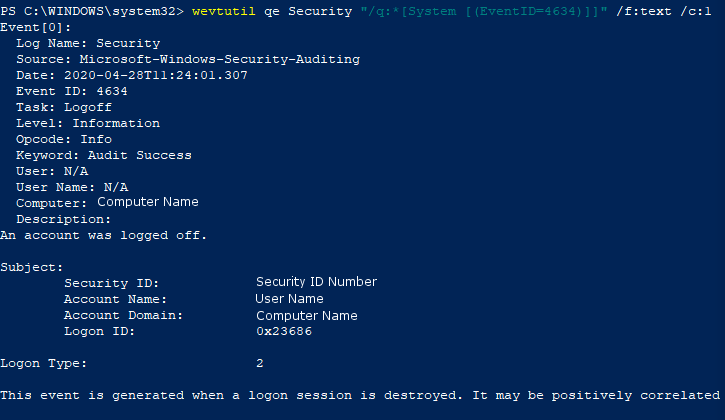
To view this log in the command line with wevtutil, open PowerShell or Command Prompt as an administrator. From here, enter the commandwevtutil qe Security "/q:*[System [(EventID=4634)]]"