Account Changed
Windows Event ID: 4738
Enabled by default
Service: Microsoft Windows Security auditing
Log type: Security
Account changes, such as password and username changes may indicate a successful breach and a backdoor setup for a user. This log also can be used to track changes for legitimate users.
View Logs
Get-WinEvent -FilterHashTable @{LogName='Security';ID='4738'}Check Logging Status
auditpol /get /subcategory:"computer account management"
Disable Logging
auditpol /set /subcategory:"computer account management" /Success:Disable /Failure:Disable
Enable Logging
auditpol /set /subcategory:"computer account management" /Success:Enable /Failure:Enable
Language: Powershell
Back to WindowsCompliance
HIPAA
Level: Recommended
PCI DSS
Level: Required
https://www.pcisecuritystandards.org/document_library?category=pcidss&document=pci_dss
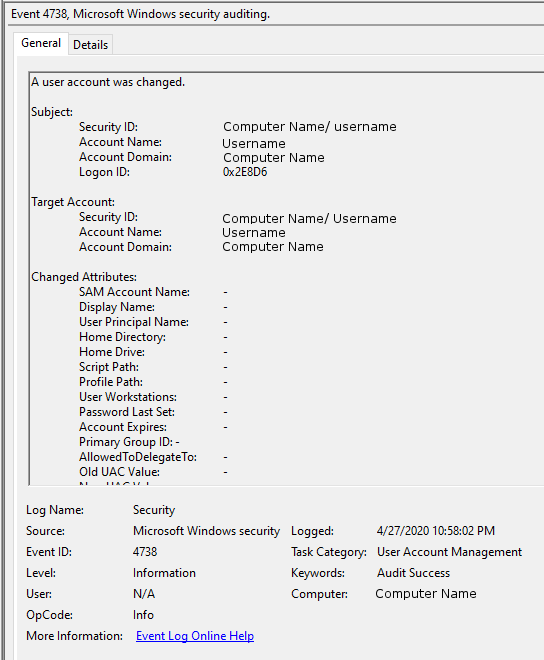
Changes made to an account are logged by default in Windows 10 Professional. To view the logs, navigate to the Event Viewer Security tab and sort of filter by Event ID 4738.
To view this log in the command line with Get-WinEvent, open PowerShell as an administrator. From here, enter the command
Get-WinEvent -FilterHashTable @{LogName='Security';ID='4738'}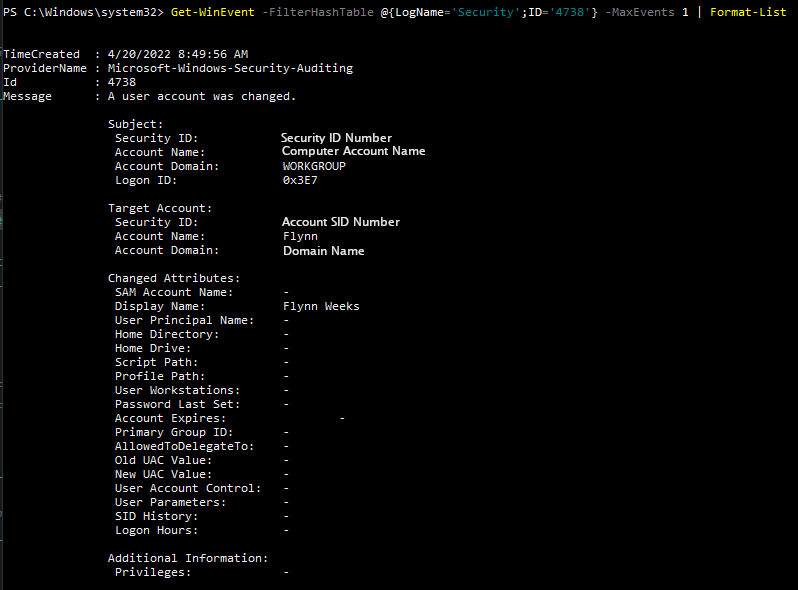
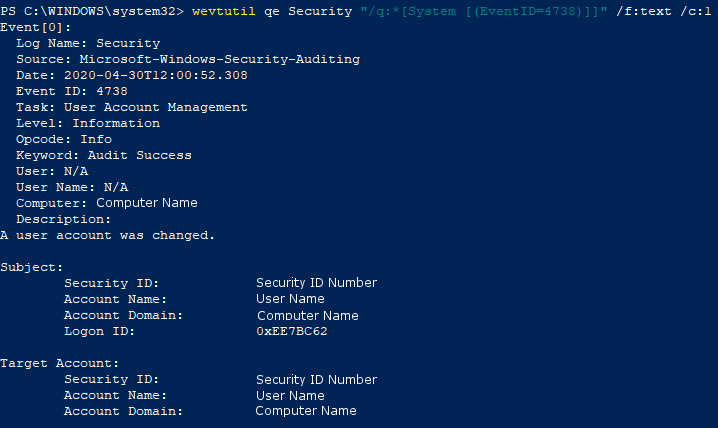
To view this log in the command line with wevtutil, open PowerShell or Command Prompt as an administrator. From here, enter the command
wevtutil qe Security "/q:*[System [(EventID=4738)]]""